- A TechNote on Information Security
- Dirk Racey, Private Security Investigator/Observer
Last year, a virus infiltrated my PC and tried to force it to call out to a hacker's server somewhere in the Republic of Moldova. If my Norton software and Windows firewall hadn't blocked the virus's incessant attempts to "call home," my PC would have pulled in still more malware, including keyboard trackers to capture my user IDs, passwords and financial account numbers. Since the attack came from a supposedly "safe" Web site that I had visited, the same could have happened to any PC or server under an IT manager's care.
Then last week, I received four official-looking phishing emails supposedly from Norton/Symantec offering steep discounts on my next subscription renewal. But while the good folks at Norton are HQ'd in California, the bogus emails (using official graphics probably snatched from Norton's own site) came from China, Russia, Africa and Eastern Europe.
 And how do I know this?
And how do I know this?
Because I trace attacks and phishing messages. You can too and you should strike back by alerting interested authorities. I especially encourage this for all virus attacks and for emails that pretend to come from organizations with which you do business, such as:
These firms want to know when someone is trying to violate your (and their) security by "spoofing" them. And many of their own Web sites offer dedicated pages for reporting attacks. But you can also report the violations to interested agencies for further investigation. This applies to both individuals who experience attacks at home and IT managers who struggle to maintain their organizations' defenses.
Track the Bastards Down
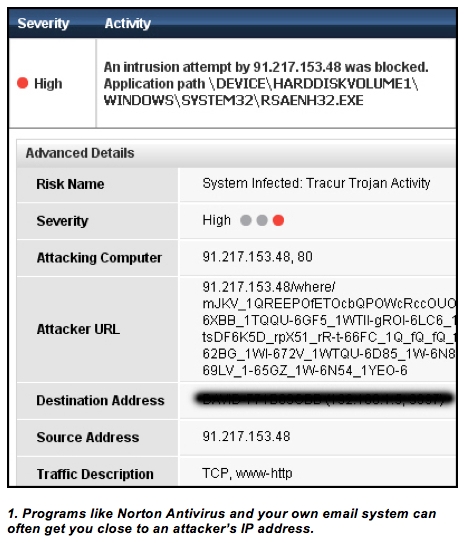
 When a computer is attacked, it's often possible to obtain an IP address that's close to the attacker's location. Intrusion alerts from programs like Norton, McAfee and Malwarebytes often provide the best address they can. And you can find similar information in the "full tracking headers" or "message sources" of email messages. These headers have different names in different email systems and are viewed in different ways. But once you determine how to open a full header in your email system, search it for a "from" or "source" IP and trace that address.
When a computer is attacked, it's often possible to obtain an IP address that's close to the attacker's location. Intrusion alerts from programs like Norton, McAfee and Malwarebytes often provide the best address they can. And you can find similar information in the "full tracking headers" or "message sources" of email messages. These headers have different names in different email systems and are viewed in different ways. But once you determine how to open a full header in your email system, search it for a "from" or "source" IP and trace that address.
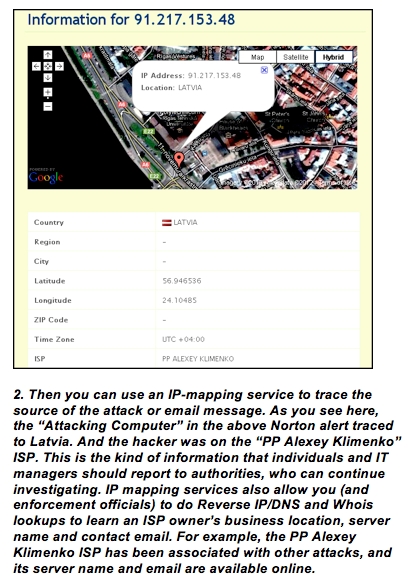
To do so, slip the address into a few of the many Web services that map IP locations. My current favorites (in this order) are:
They'll probably map the address to slightly different locations. That's because each service uses a different geolocation database and tries to find the Internet router that's closest to the target IP. The accuracy of the result depends on the database used and the number of known routers in the target IP area.
For example, I just traced my own PC's IP address, and these services mapped it to Medford, Mass.; downtown Boston, and, yes, just down the road in my own hometown. But all locations were within 6 miles of my PC, so the results were pretty darned accurate. Your traces may get equally close to the attackers' locations (and might also tell you the ISPs they are using).
Then Report 'Em
With this information in hand, you can (and should) nail the e-criminals by reporting them to interested authorities. These men in black have tools and powers we don't, such as the ability to obtain court orders for detailed ISP records. In addition to the organizations mentioned earlier, you should report hackers' IP addresses, IP map locations and ISPs to:
By alerting experts like these, you'll help shield other PCs and networks (including your own) from the same and similar attacks because they'll make their way into the malware signature identification capabilities of the scanners we all use. If you don't report attacks you'll only be allowing them to continue.
And Now, I'm Taking a Little Trip
The world has seen a strong up-tick in distributed-denial-of-service attacks. IP managers across the globe are probably losing sleep over them. So ol' Dirkie is slipping undercover for a few months to investigate DDOS perpetrators, solutions and even potential counter-attacks. It may be a harrowing trip, but I hope to return here--propped up against my favorite lamppost-- very soon. Wish me luck!
Then last week, I received four official-looking phishing emails supposedly from Norton/Symantec offering steep discounts on my next subscription renewal. But while the good folks at Norton are HQ'd in California, the bogus emails (using official graphics probably snatched from Norton's own site) came from China, Russia, Africa and Eastern Europe.
 And how do I know this?
And how do I know this? Because I trace attacks and phishing messages. You can too and you should strike back by alerting interested authorities. I especially encourage this for all virus attacks and for emails that pretend to come from organizations with which you do business, such as:
- Banks
- Apple
- Microsoft
- Amazon
- Ebay/PayPal
- The IRS
- Security vendors (like Norton/Symantec, McAfee and Malwarebytes)
These firms want to know when someone is trying to violate your (and their) security by "spoofing" them. And many of their own Web sites offer dedicated pages for reporting attacks. But you can also report the violations to interested agencies for further investigation. This applies to both individuals who experience attacks at home and IT managers who struggle to maintain their organizations' defenses.
Track the Bastards Down
 When a computer is attacked, it's often possible to obtain an IP address that's close to the attacker's location. Intrusion alerts from programs like Norton, McAfee and Malwarebytes often provide the best address they can. And you can find similar information in the "full tracking headers" or "message sources" of email messages. These headers have different names in different email systems and are viewed in different ways. But once you determine how to open a full header in your email system, search it for a "from" or "source" IP and trace that address.
When a computer is attacked, it's often possible to obtain an IP address that's close to the attacker's location. Intrusion alerts from programs like Norton, McAfee and Malwarebytes often provide the best address they can. And you can find similar information in the "full tracking headers" or "message sources" of email messages. These headers have different names in different email systems and are viewed in different ways. But once you determine how to open a full header in your email system, search it for a "from" or "source" IP and trace that address. To do so, slip the address into a few of the many Web services that map IP locations. My current favorites (in this order) are:
- http://www.liveipmap.com
- http://www.ip-address.com
- http://www.whatismyip.com/tools/ip-address-lookup.asp
They'll probably map the address to slightly different locations. That's because each service uses a different geolocation database and tries to find the Internet router that's closest to the target IP. The accuracy of the result depends on the database used and the number of known routers in the target IP area.
For example, I just traced my own PC's IP address, and these services mapped it to Medford, Mass.; downtown Boston, and, yes, just down the road in my own hometown. But all locations were within 6 miles of my PC, so the results were pretty darned accurate. Your traces may get equally close to the attackers' locations (and might also tell you the ISPs they are using).
Then Report 'Em
With this information in hand, you can (and should) nail the e-criminals by reporting them to interested authorities. These men in black have tools and powers we don't, such as the ability to obtain court orders for detailed ISP records. In addition to the organizations mentioned earlier, you should report hackers' IP addresses, IP map locations and ISPs to:
- The FBI. Mouse over the SCAMS & SAFETY tab at the top of the page, and select Report Internet Crime. This opens their Internet Crime Complaint Center (IC3). Click the big red "File a Complaint " link at the bottom of the IC3 page, provide all requested information, and tell them everything you've learned about the hackers and their attack.
- The US-CERT Incident Reporting System. As with the FBI, tell CERT everything you know abut the intrusion.
- BroadbandDSLReports.com. They offer great security info for IP managers here and collect attack reports (and even Zipped malware files) here.
- The Federal Trade Commission, which offers a ton of infosecurity information here and collects identity-theft complaints here.
- Your own anti-virus/malware and firewall vendors, so they can research and respond to any new intrusions that you see.
By alerting experts like these, you'll help shield other PCs and networks (including your own) from the same and similar attacks because they'll make their way into the malware signature identification capabilities of the scanners we all use. If you don't report attacks you'll only be allowing them to continue.
And Now, I'm Taking a Little Trip
The world has seen a strong up-tick in distributed-denial-of-service attacks. IP managers across the globe are probably losing sleep over them. So ol' Dirkie is slipping undercover for a few months to investigate DDOS perpetrators, solutions and even potential counter-attacks. It may be a harrowing trip, but I hope to return here--propped up against my favorite lamppost-- very soon. Wish me luck!













Trending Discussions
- If you would like to see the other articles in the blog post of the "Top Ten VoIP Articles of All Ti... Steven Taylor, Webtorials on "Is VoIP Secure? YOU Make the Call":
- Great job I followed since the begining thanks... Eduardo Pérez Telesystems SpA on "The 2018 Guide to WAN Architecture and Design - Executive Summary":
- Thanks to Marjorie at RingCentral for reminding me that this paper existed. Looking forward to your... Steven Taylor, Webtorials on "Is VoIP Secure? YOU Make the Call":
- looking at WAN re-engineering projects... Sunny on "The 2018 Guide to WAN Architecture and Design - Part 2: Key Considerations when Choosing new WAN and Branch Office Solutions":
- Hi Richard. We appreciate your feedback. Jim Metzler always provides excellent analysis on the ever-... Nancy Leonard, Webtorials on "The 2017 State-of-the-WAN Report":
- Interesting reading... Richard Fausey, Plow, LLC on "The 2017 State-of-the-WAN Report":
- I needed this document. Thank you.... AO NII Mashtab on "The 2017 Guide to WAN Architecture and Design - Executive Summary":
- I look forward to reviewing more info on this topic.
... trevor evans - fox group on "2017 Workplace Productivity and Communications Technology Report":
- I would like access to your "2017 Workplace Productivity and Communications Technology Report"
Than... Paul Zielie, Harman Professional Solutions on "2017 Workplace Productivity and Communications Technology Report":
- I'm Telecommunications Engineer at PETROBRAS S.A. and i have overall interest about WAN. ... JOSE CEREZO, PETROBRAS S.A. on "The 2017 Guide to WAN Architecture and Design - Part 1: State of the WAN":
See more discussions...